Recently, there have been scammers using blockchain forks to steal private keys, and thus crypto assets, from unsuspecting users. We wanted to outline the steps you can take to not only protect your assets before and after a fork, but also how to safely claim your forked coins without getting your original coins stolen.
Blockchain Fork Explained
Before we get into what happens during a fork and its potential security risks, we first need to understand what a blockchain is. A blockchain is a decentralized and distributed ledger where data and transactions can only be appended to it. Once appended, they are permanent — they cannot be changed, overwritten, or erased. Bitcoin and cryptocurrencies (altcoins) run on blockchain technology.
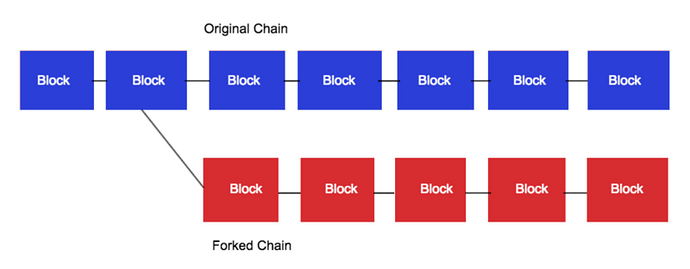
A blockchain fork is when one chain splits into two separate chains that share the same transaction ledger history — hence the term “fork”. Depending on the type of fork (there are a few different types — hard fork, soft fork, user-activated fork, and so on), the rules that determine whether a transaction or block is valid may change. Blocks created using the old set of rules may be deemed invalid, and miners will mine the new chain with the longest history of valid transactions. The old chain would therefore be abandoned by these miners.
Illustration credits to Hackernoon
When a project hard-forks its chain to a new one, they produce a 1:1 copy of the original coins. However, wallet users need to provide their private keys in order to claim the forked coins. For reasons explained below, this can be extremely risky.
How Scammers Can Use a Fork to Steal Your Private Keys
A possible scenario is where a project is about to conduct a hard fork and provide a link for you to supply your private keys to “claim” the forked coins. However, this may be a scam, because the URL could send your private keys to a remote server owned by the perpetrators of the scam. The objective of these perpetrators is to gain control of your wallet and thus obtain all of your tokens.
There have been a couple of recent cases involving the alleged forks of Ethereum Classic Vision and Ethereum Nowa that disguised scam attempts to steal private keys from unsuspecting wallet users. After analyzing the deception, according to Guarda, Ethereum Nowa “is a way for the thieves to get your private information and gain access to your wallet.”
Steps to Protect Your Coins During a Fork
Things change quickly in the blockchain industry, so sometimes there is a lot of confusion about what’s true and what’s not. It can be difficult to distinguish a legitimate fork from a scam that attempts to trick users to divulge their private keys. If you’re holding a coin that’s about to undergo a hard fork, you are encouraged to do your due diligence and take a precautionary approach should you want to claim the forked coins.
Below are the steps to take if you want to claim your forked coins without jeopardizing the original coins in your wallet.
Before the Fork
Because there are a couple of steps you need to do before the project forks, it is important to stay up to date on the projects of which coins you hold.
● Step 1: Create a (1) new wallet to use with the forked chain. Wallet in Crypto Exchange not recommended.
● Step 2: Transfer your original coins to that new wallet.
After the Fork
● Step 3: Transfer the original coins back to original wallet IMPORTANT!
● Step 4: If necessary, provide private keys of new wallet to claim the forked coins.
● Step 5: Use new wallet to transact with the forked coins.
As an extra security measure, you may optionally create another (2) new wallet and transfer the forked coins to that wallet and discontinue using the (1) new wallet if you have shared your private keys of (1) new wallet.
Closing Remarks
If the fork was legitimate, you would still be able to claim the forked coins as the wallet transaction history is the same up to the forked block. Plus, security-conscious projects undergoing a fork would not conduct such transition by asking users to provide their private keys to their wallets at any point in time.
(Author: Nobel Tan, Sentinel Protocol)